If you are looking for Office 365 | FAR Networks you've came to the right page. We have 8 Pics about Office 365 | FAR Networks like How ...
If you are looking for Office 365 | FAR Networks you've came to the right page. We have 8 Pics about Office 365 | FAR Networks like How G Suite protects your data - Tangerine - Tangerine, Hybrid Infrastructure Design – Allianz Cloud and also Office 365 | FAR Networks. Read more:
Office 365 | FAR Networks
 farnetworks.com
farnetworks.com 365 office diagram flexibility choice
How G Suite Protects Your Data - Tangerine - Tangerine
 www.tangerine.co.th
www.tangerine.co.th tangerine protects
PCI DSS Compliance | Shieldbyteinfosec.com
 shieldbyteinfosec.in
shieldbyteinfosec.in dss compliance
Federal PKI Security Challenges: Protecting Machine Identities | Venafi
 www.venafi.com
www.venafi.com challenges why security pki federal venafi machine iot identities encryption backdoors shave exploit mandate eager legislators protect enough doing identity
9 Flaws Of Automated Web Application Vulnerability Scanners - CDW
 expertswhogetit.ca
expertswhogetit.ca scanners vulnerability flaws
Sophos Central Intercept X Advanced - 1-9 USERS - 36 MOS - Tech Data
 www.innovixmarketplace.com
www.innovixmarketplace.com sophos intercept
Hybrid Infrastructure Design – Allianz Cloud
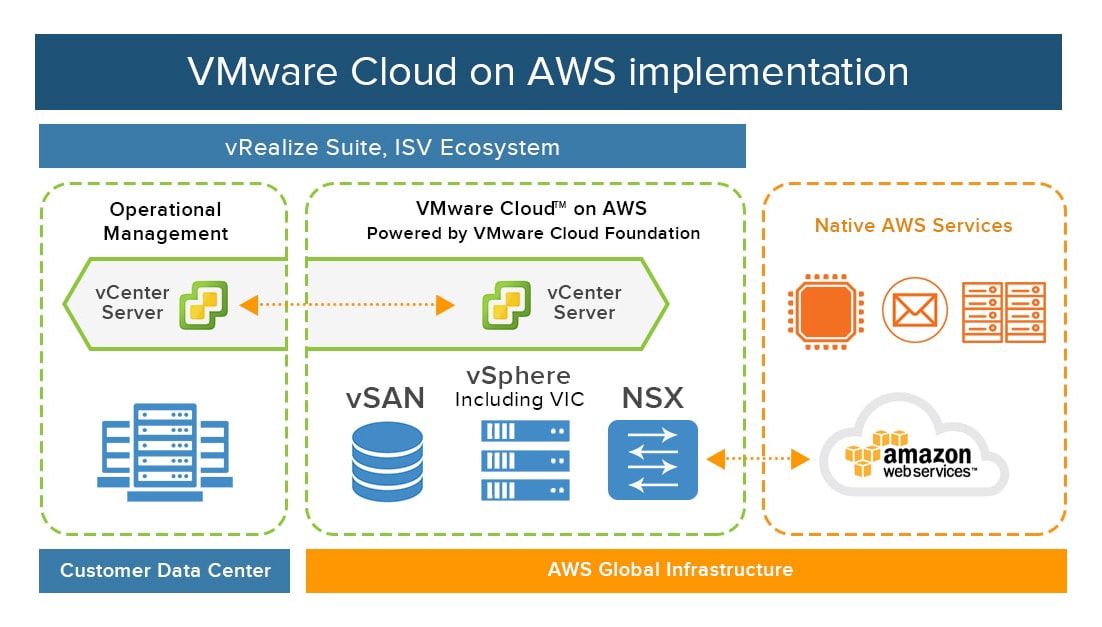 allianzcloud.com
allianzcloud.com Infrastructure Design - Infrastructure Optimization, Migration
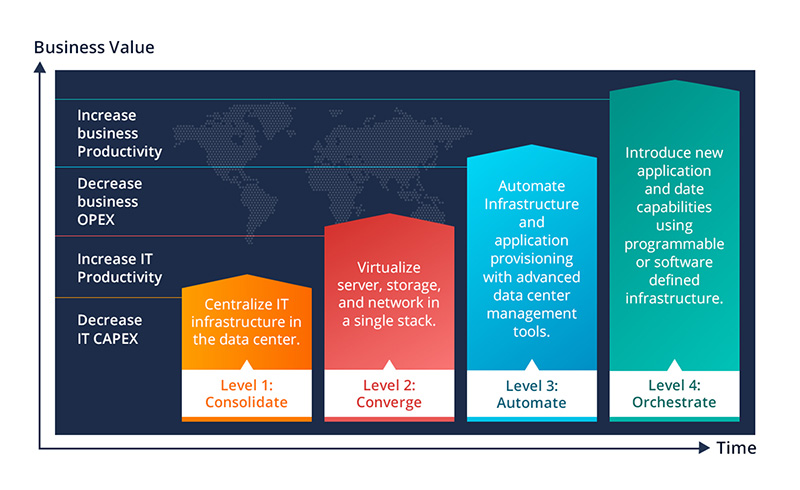 www.hashroot.com
www.hashroot.com infrastructure optimization migration
Dss compliance. Tangerine protects. How g suite protects your data




COMMENTS